Configuration Management
- Home -
- Configuration Management
Configuration Management
CLOUD SECURITY
The implementation of continuous monitoring software is aimed at enhancing the visibility and transparency of network activity, particularly suspicious network activity that may suggest a security breach, in order to mitigate the risk of cyber attacks using a timely alert system that triggers rapid incident response. To enable organizations to effectively monitor network traffic, detect anomalies or suspicious patterns of activity, and develop actionable insights, software vendors offer robust and versatile solutions.
The implementation of a continuous monitoring software solution typically involves five basic steps:
OUR IMPLEMENTATIONS
- Defining the system
- Assessing risks
- Selecting security control applications
- Implementing those applications
- Configuring software tools
- Ongoing assessment
Automated
monitoring
- Pinpoint areas of concern
- Automated auditing
- Risk management entails action
- Dynamic control tracking
- Introduce enhanced compliance requirements
- Real-time transaction analysis
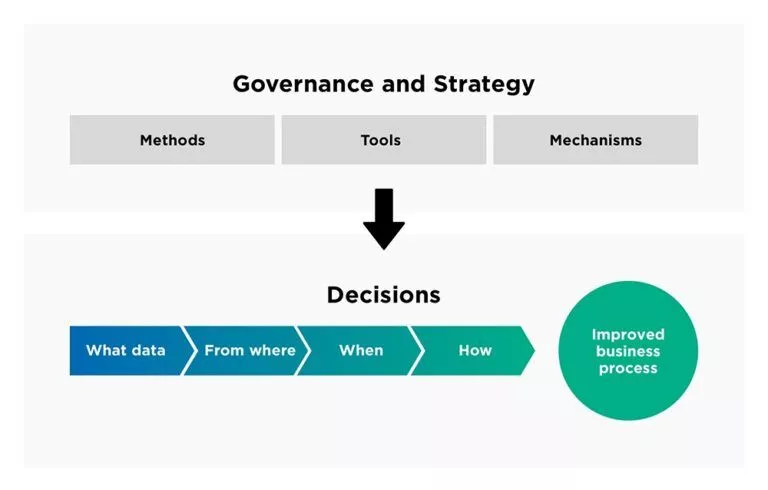
Integrated governance approach
Collaborating for agility: IT and business partnerships that deliver results