Cyber & Security Operations
- Home -
- Cyber & Security Operations
CLOUD SECURITY
CLOUD SECURITY
Our team understands the importance of protecting your data in the cloud. That's why we offer comprehensive cloud security solutions that ensure your information is always safe and secure.
With our cloud security services, you can rest assured that your business data is protected from unauthorized access, data breaches, and other threats. Our team uses the latest technology and security protocols to keep your information safe.
Whether you’re moving to the cloud for the first time or need help enhancing your existing cloud security measures, our team can help. We offer a range of services, including security assessments, risk analysis, and ongoing monitoring and management.
At UTG, we believe that cloud security should be a top priority for every business. That’s why we offer customized solutions that are tailored to your specific needs and requirements. Our team will work with you to identify potential threats and vulnerabilities, and implement strategies to mitigate those risks.
When it comes to cloud security, you need a team that you can trust. Our experienced professionals have the expertise and knowledge to help you navigate the complex world of cloud security. We’ll work with you to develop a customized solution that meets your unique needs and budget.


collaborative security measures
At UTG, we believe that security is a shared responsibility between the client and the provider. While the cloud provider is responsible for the physical infrastructure and security of the applications, the client is responsible for authorizing and controlling their own cloud environment. We work closely with our clients to establish clear security protocols and procedures to ensure that their data is always protected. Our team is dedicated to staying up-to-date on the latest security threats and developments in the industry to provide our clients with the highest level of protection possible. We understand that each client has unique security needs, which is why we offer customized solutions that are tailored to their specific requirements. Whether it's conducting regular security assessments or implementing new security measures, our team is committed to working with our clients every step of the way to ensure their security needs are met.
Collaborate with us!
If you are interested in our services, please send us an inquiry and we will respond promptly.
MOBILE SECURITY

MOBILE SECURITY
At UTG, we know how important mobile security is in today's world of technology. That's why we offer best-in-class mobile application management services to help keep your data safe and secure. Our team of experienced professionals uses the latest tools and technologies to deliver amazing results on any device. We specialize in custom app development with a particular focus on security, scalability, and interoperability. Our mature application development process covers the entire software development life cycle and provides a stable environment and framework for our clients. We are committed to staying up-to-date on the latest mobile security threats and developments in the industry so that we can provide our clients with the highest level of protection possible. Whether it's developing new apps or optimizing existing ones, our team is dedicated to helping our clients achieve their business objectives while keeping their data safe.
Mobile security infrastructure
Mobile security infrastructure
- Virtual Private Network (VPN)
- Mobile Device Management (MDM)
- Mobile Application Management (MAM)
- Identity and Access Management (IAM)
- Mobile Application Store (MAS)
- Mobile Application Gateway (MAG)
- Data Loss Prevention (DLP)
- Intrusion Detection System (IDS)
- Gateway and Security Stack (GSS)
Our Enactments
At UTG, we believe that a comprehensive security architecture is essential to protecting an organization's assets. To achieve this, we focus on three key components: people, process, and technology. Our team works closely with clients to identify potential security risks and vulnerabilities, and develop strategies to mitigate them. We understand that policies are a critical component of any security architecture, so we work with clients to establish clear policies and procedures that are enforceable and effective. Our implementation methodology is designed to be as seamless as possible, minimizing potential disruptions to business operations. From start to finish, our team is dedicated to designing and implementing a security architecture that provides maximum protection for our clients' data and assets.

01
Ensuring compliance and security through effective policy and procedure implementation.
02
Empowering users with secure access to the digital resources they need.
03
Secure and seamless access to digital assets through cutting-edge technology and effective policies.

04
Staying ahead of the curve with agile policy and regulatory updates in a rapidly evolving technological landscape.
ZERO TRUST
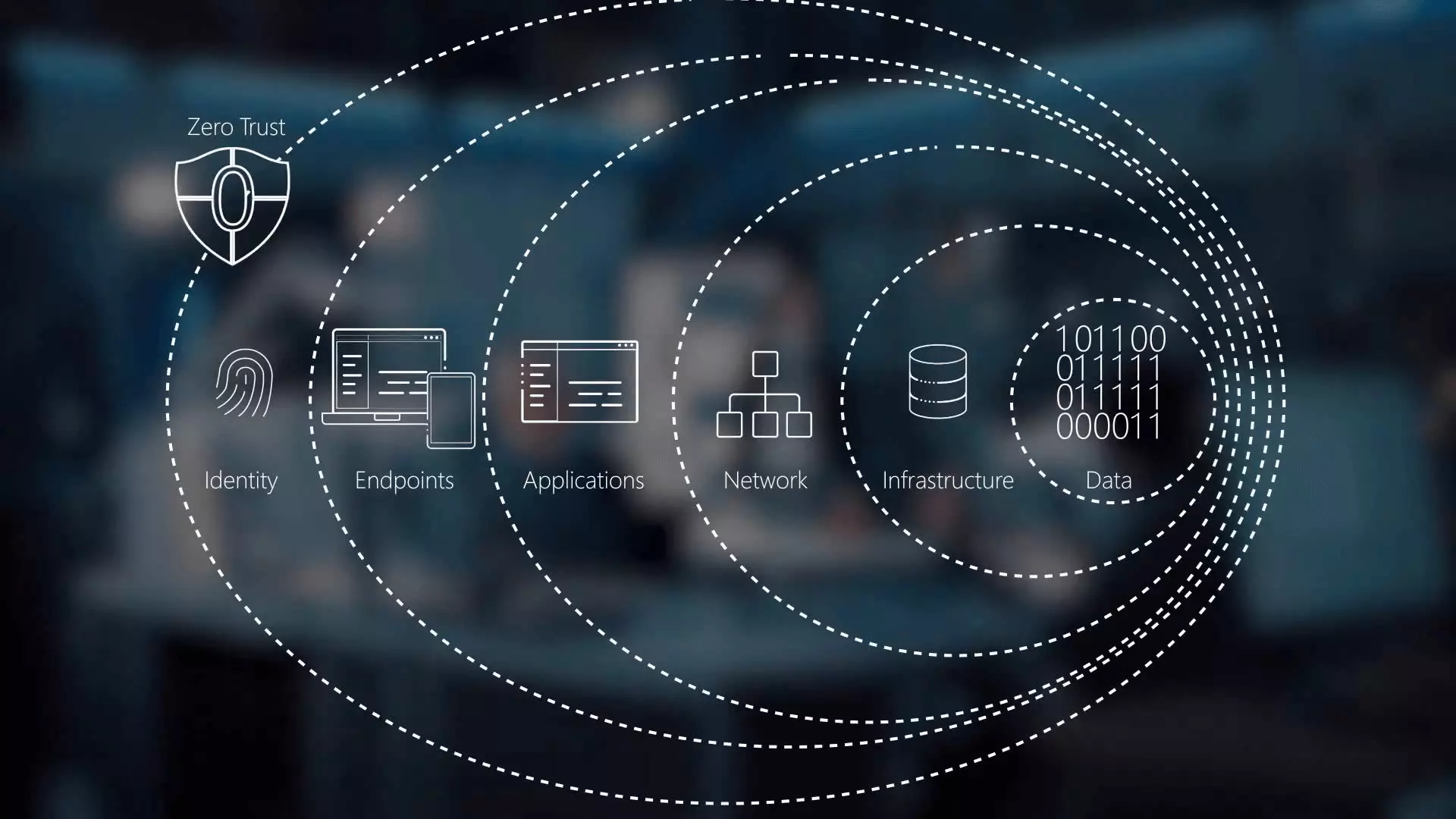
Least privilege(Zero-Trust)security
We understand the importance of implementing a Zero Trust security approach to protect organizations from cyber threats. By eliminating implicit trust and continuously validating every stage of a digital interaction, our Zero Trust strategy provides a comprehensive and proactive approach to cybersecurity. Our team uses strong authentication methods and constantly monitors for potential threats to ensure that our clients' data and assets are always protected. As digital transformation continues to accelerate, with a growing hybrid workforce and increasing migration to cloud environments, a Zero Trust approach has become more critical than ever before. At UTG, we are committed to helping our clients stay ahead of potential threats and keep their systems secure with cutting-edge Zero Trust solutions.
Advantage
ZERO TRUST
SECURITY
- Optimized security protocols
- Standardized environment
- Lowered budget outlay
